ChaosSearch leverages best practices and technologies to deliver a highly secure service, including encrypting data in transit, support RBAC and SSO, and using storage-based isolation directly within your cloud object storage.
Single Sign On (SSO)
ChaosSearch supports Single Sign On (SSO) as a session and user authentication service that permits a user to use one set of login credentials (e.g., name and password) to access multiple applications. SSO can be used by enterprises, smaller organizations, and individuals to mitigate the management of various usernames and passwords.
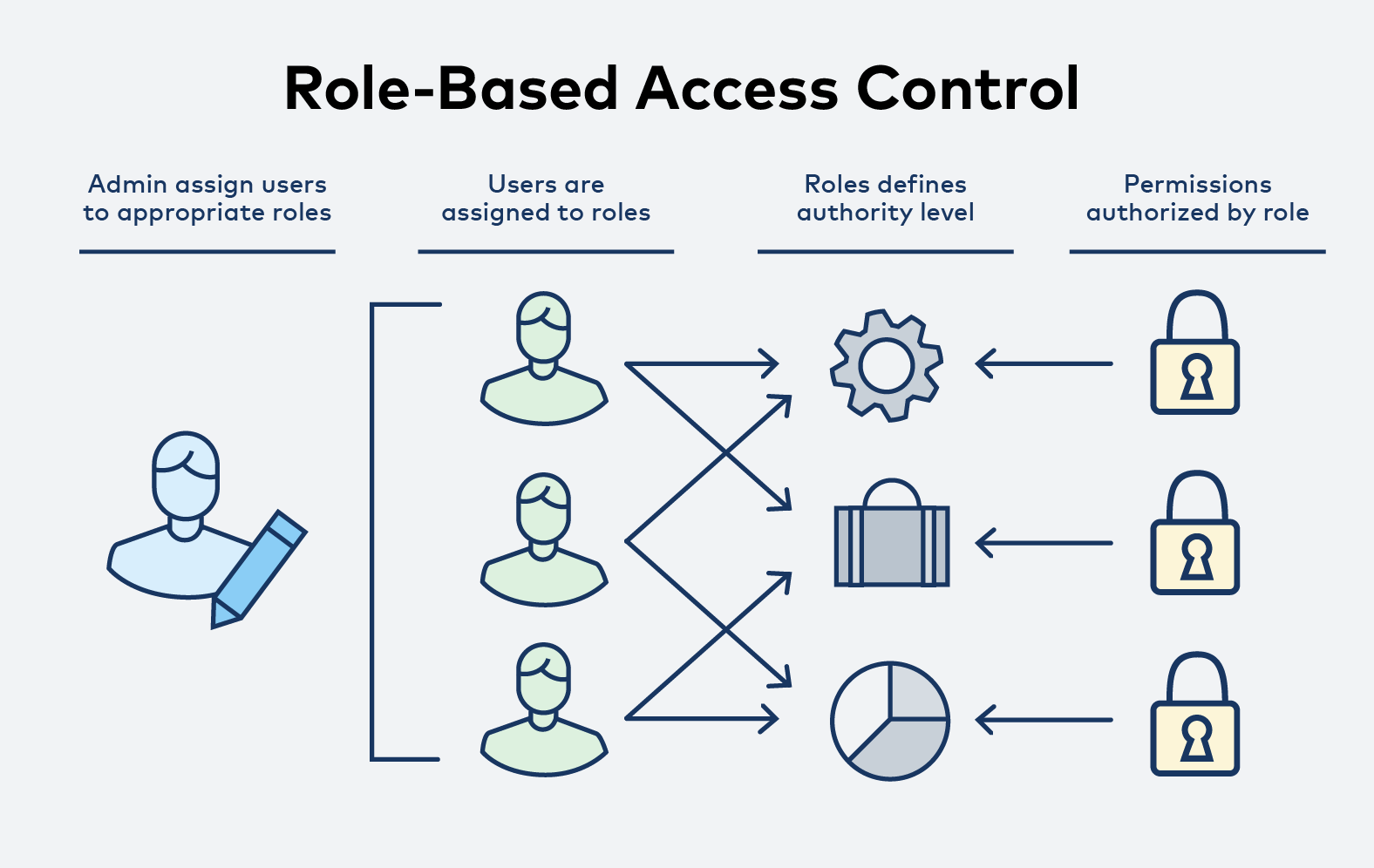
Role-Based Access Control (RBAC)
Granular, role-based access control (RBAC) enables you to control the actions a user can perform within the ChaosSearch platform. Among other items, roles control access to functions, data, and even documents. ChaosSearch RBAC also supports multi-tenant environments, allowing multiple teams to share the environment while only being able to access their team's data and dashboards.
Encryption
Encryption in-transit is essential to prevent your data from being intercepted when moving between ChaosSearch and your Amazon S3. ChaosSearch supports OpenSSL and TLS 1.2, allowing you to meet stringent security and compliance requirements.
Audit Logging
With audit logging, you can record and track all the actions performed by users in your ChaosSearch environment and monitor any suspicious activity, which is essential for security incident response. Audit logging also helps you remain compliant with government and industry regulations such as GDPR, HIPAA, PCI, and ISO.
Storage-Based Isolation
ChaosSearch leverages Amazon S3 and its associated access control policy constructs to isolate customers. The ability to control visibility from the storage layer (i.e. where the data actually resides), in a central location, is the most secure and simplest mode to operate. And with S3’s advanced Identify and Access Management (IAM) functionality and roles, the combination of storage-base folder structure isolation together with an IAM’s Role Based Access Control (RBAC) overlay, delivers exceptional security.
Additional Resources
- Please visit our security page for information on our security and compliance certifications.
- Read the ChaosSearch Solution Brief
- Read the whitepaper: A Detailed Look at ChaosSearch
©2024, ChaosSearch®, Inc. Legal
Elasticsearch, Logstash, and Kibana are trademarks of Elasticsearch B.V., registered in the U.S. and in other countries. Elasticsearch B.V. and ChaosSearch®, Inc., are not affiliated. Equifax is a registered trademark of Equifax, Inc.





