Why Log Analytics is Key to Unlocking the Value of XDR for Enterprises
Cyber threats are becoming more sophisticated, and enterprise security teams are under constant pressure to improve and enhance their threat detection and response capabilities.
But as security teams expand their security logging tools and capabilities, the burden of monitoring those tools and investigating alerts grows exponentially. In many cases, more security tooling means more false positives that generate “alert fatigue”, discouraging security teams from investigating alerts and potentially worsening an organization’s security posture.
Enter Extended Detection and Response (XDR): a new enterprise security solution that integrates security data and alerts from throughout an organization’s IT systems, making it easier for security teams to detect and respond to threats.
In this blog, we’ll explore what XDR solutions are, how they use log analytics to deliver enhanced threat detection, and how a security data lake complements your XDR solution to enhance enterprise cyber security.

What is XDR?
XDR is a next-gen cyber security technology that improves the threat detection and response capabilities of organizations by providing a holistic view of security across multiple environments, including endpoints, networks, and cloud workloads.
XDR is an evolution of traditional security tools like Endpoint Detection and Response (EDR) and Network Detection and Response (NDR). XDR solutions extend the capabilities of these tools by ingesting, integrating, and correlating security logs and telemetry data from a variety of sources, including cloud applications and services, email security gateways, firewalls, log management and SIEM tools, and IAM systems.
By correlating security data from multiple sources, XDR solutions can identify threats that may have been missed by traditional security tools and provide a more complete picture of the attack lifecycle.
XDR solutions typically use advanced analytics and machine learning algorithms to detect and respond to threats in real-time. When a threat is detected, XDR solutions help automate and orchestrate the incident response process, allowing security teams to quickly contain and remediate threats. They also provide a centralized dashboard where security operations center (SOC) teams can monitor security events across the organization and prioritize alerts based on their severity.
XDR solutions provide a more comprehensive and integrated approach to threat detection and response, improving the overall security posture of organizations in the face of increasingly sophisticated and persistent threats.
Log Analytics Unlocks the Value of XDR
XDR solutions are revolutionizing how organizations approach security threat detection and response by providing a unified view of security across multiple environments. The key to success for XDR solutions is log analytics: the ability to collect and correlate log data from multiple sources within the organization at scale, then analyze those logs in real-time to deliver prioritized alerts and insights to SOC teams.
XDR solutions apply log analytics to an integrated data set that includes security alerts from other tools and rich device, network, and cloud logs. By analyzing and correlating logs from multiple data sources, XDR solutions can identify anomalous behavior and indicators of compromise that might have been missed by traditional security tools. This capability helps organizations detect and respond to threats faster and with greater accuracy, minimizing the risk of a successful cyber attack.
How Do XDR Solutions Work?
Modern XDR solutions are cloud-native Software-as-a-Service (SaaS) products. These solutions deploy in the cloud and integrate with other security tools and systems to centralize the data they provide. XDR customers typically pay a monthly subscription fee to the software vendor and may incur additional costs based on the total volume of data they ingest.
Keep reading to learn more about the important functions XDR systems fulfill.
Integrates Security Data from Multiple Sources
XDR solutions centralize security alerts from integrated security tools, monitor device and user behavior for anomalies, and collect and aggregate security logs from enterprise devices, networks, and cloud applications.
By aggregating this data and analyzing it with machine learning and advanced log analytics, XDR solutions can provide security teams with a comprehensive view of an organization’s security posture. Acting as a centralized platform for enterprise security monitoring and alerts, XDRs help counteract false positives and alert fatigue so SOC teams can operate more efficiently.
Consolidates SOC Functions in a Single Console
Consolidating SOC functions, such as incident response, case management, threat intelligence management, threat hunting, and forensics, into a single console, XDR solutions make it easier for SOC teams to manage and respond to security incidents.
Delivers Security Automation Capabilities
XDR solutions use sophisticated technologies like machine learning and artificial intelligence to automate routine security tasks, such as threat detection and response, enabling SOC teams to focus on higher-value activities.
Helps SOC Teams Secure Enterprise IT Systems
By providing a unified view of an organization's security posture, automating routine security tasks, and streamlining SOC operations, XDR solutions enable SOC teams to more efficiently secure enterprise IT systems, reducing the risk of cyber attacks.
5 XDR Solutions You Should Know
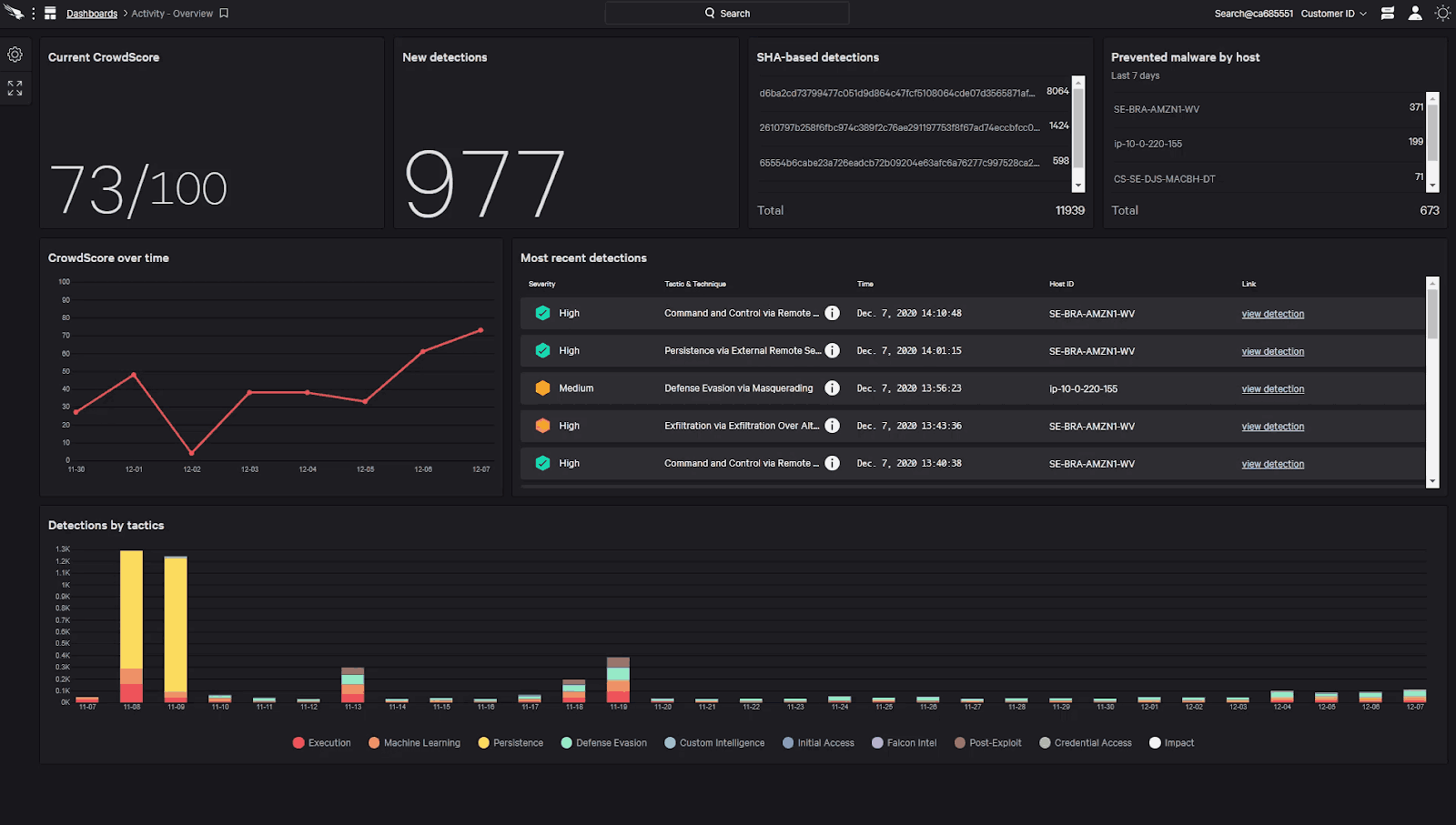
1. CrowdStrike Falcon Insight XDR
Crowdstrike Falcon Insight XDR provides comprehensive endpoint detection and response capabilities, leveraging machine learning and behavioral analytics to identify and respond to advanced threats. The platform also incorporates threat intelligence from CrowdStrike's global network to enhance detection and response.
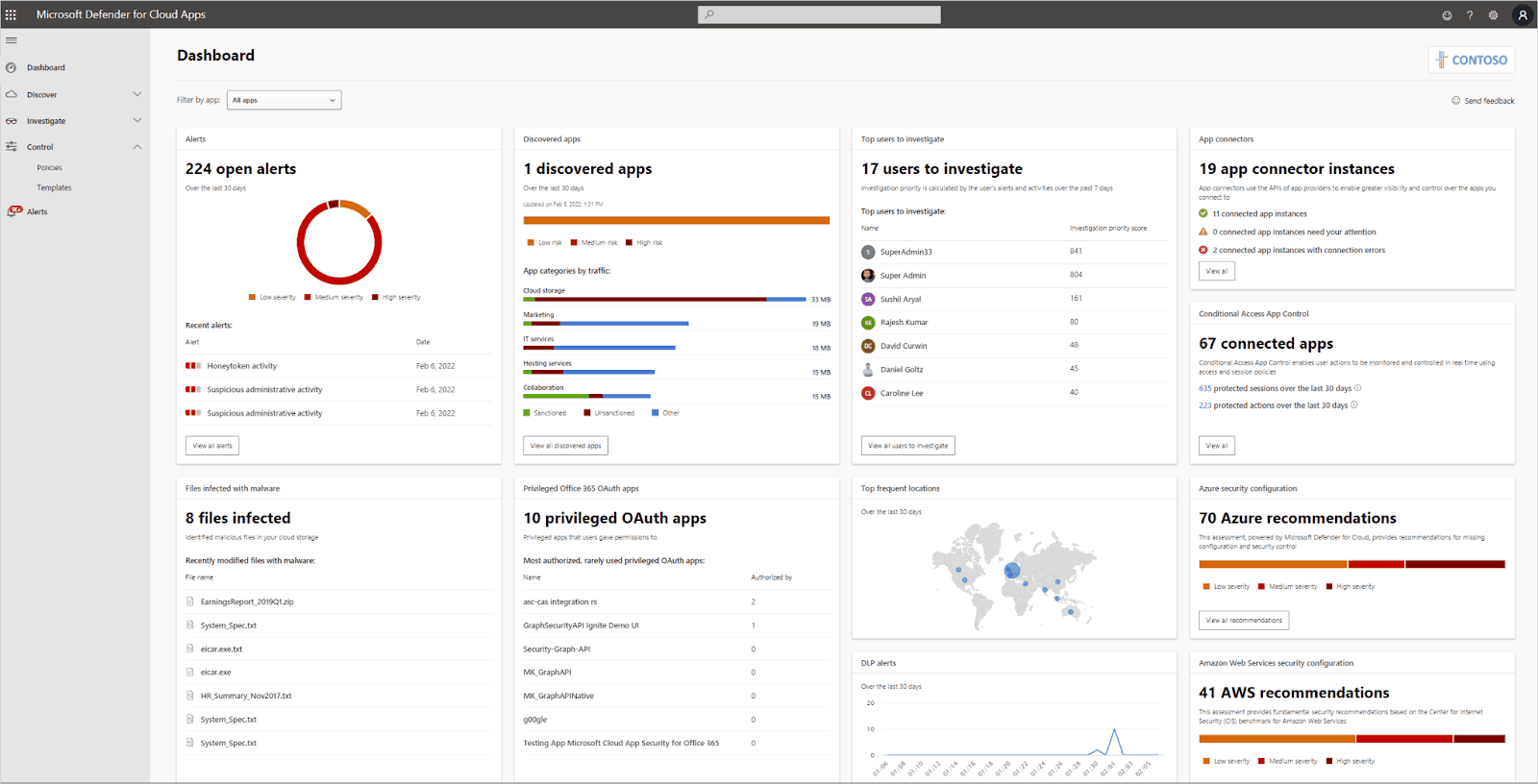
2. Microsoft 365 Defender
Microsoft 365 Defender is a cloud-native XDR solution that integrates with Microsoft's suite of security products to provide unified visibility across device and network endpoints, email, and cloud workloads. The platform uses automation and AI-driven log analytics to detect and remediate threats, while also providing proactive hunting capabilities.
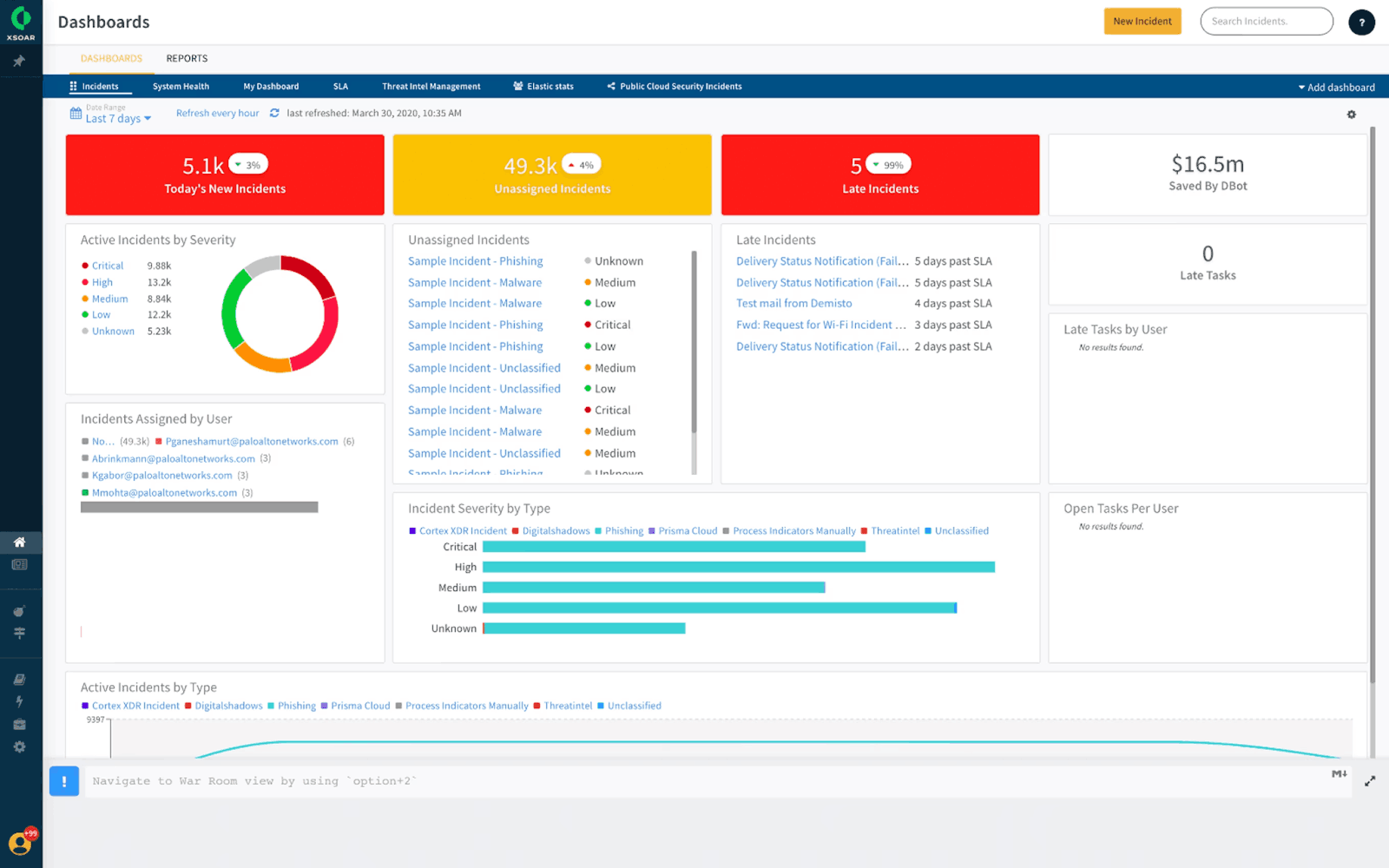
3. Palo Alto Networks Cortex XSOAR
The world’s first XDR platform, Cortex XSOAR is a security orchestration, automation, and response (SOAR) platform that provides integrated XDR capabilities. The solution enables security teams to automate repetitive tasks, orchestrate security operations workflows between hundreds of different products, and respond to threats across endpoints, networks, and cloud environments.
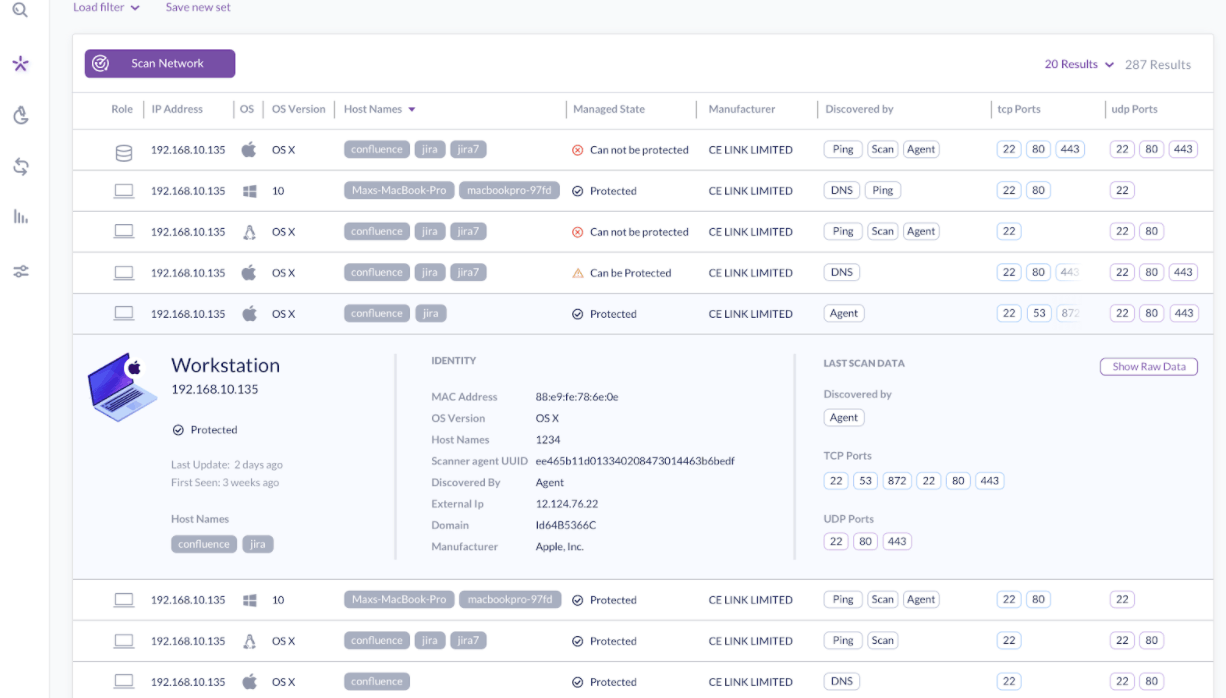
4. SentinelOne Singularity XDR
SentinelOne Singularity XDR provides AI-powered XDR capabilities that unify endpoint, cloud, and IoT security. The platform integrates data from endpoints, cloud services, and IAM systems, then uses a patented behavioral AI system to detect and respond to threats in real-time while providing security teams complete visibility and control across the entire enterprise.
5. Trend Micro Vision XDR
Trend Micro Vision XDR is a cloud-native XDR solution that provides real-time threat detection and response across the customer organization’s entire IT infrastructure. The platform feeds telemetry and log data from endpoints, email, network, servers, and cloud workloads into a data lake, then applies purpose-built AI and security log analytics to detect and respond to sophisticated attacks.
What are the Benefits of XDR Solutions?
1. Simplified security management
XDR solutions provide a unified view of an organization's security posture, consolidating security data from multiple sources and enabling SOC teams to manage security alerts and incidents in a single console.
2. Greater visibility of network security
By integrating security data from across an organization’s IT infrastructure, XDR solutions provide enhanced visibility into an organization’s overall security posture, This enables SOC teams to identify and address security gaps and vulnerabilities more effectively.
3. Improved threat detection
XDR solutions continuously profile endpoint and user behavior to detect anomalies that could indicate a cyber attack. They also apply advanced log analytics and machine learning to endpoint, network, and cloud logs to identify and prioritize security threats, enabling organizations to detect and respond to potential cyber-attacks more effectively.
4. Enhanced threat response capabilities
XDR solutions provide SOC teams with a centralized platform to investigate and respond to security incidents across an organization's IT infrastructure, streamlining the incident response process and reducing mean time to remediation.
5. Increased SOC efficiency and reduced costs
By automating routine security tasks, consolidating SOC functions, and providing a more comprehensive view of an organization's security posture, XDR solutions help SOC teams operate more efficiently and reduce the overall cost of managing enterprise IT security.
Read: Integrating Observability into Your Security Data Lake Workflows
Complement Your XDR Solution with a Security Data Lake
XDR solutions are effective at correlating security and event logs from across an organization’s IT infrastructure to detect threats in real-time, but the long-term data retention needed to support use cases like APT detection and root cause analysis can get very expensive - especially for organizations producing a large amount of data every day.
That’s why it makes sense to complement the real-time threat detection and response capabilities of XDR solutions with the long-term cloud data retention and analytics capabilities of a security data lake.
Creating a cloud-based security data lake with a solution like ChaosSearch gives SOC teams the ability to cost-effectively store critical security logs with no limits on data ingestion or retention.
ChaosSearch transforms your AWS or GCP cloud object storage into an activated security data lake, enabling long-term security analytics and compliance use cases. Ship log data from your IT infrastructure into Amazon S3 and ChaosSearch will automatically index your data with up to 95% compression. From there, you can query your log data with full-text search or SQL, apply virtual transformations, and create virtual views or dashboards with no data movement or duplication.
Establishing a security data lake with ChaosSearch can reduce the TCO of your XDR solution while providing additional use cases and capabilities that strengthen your organization’s approach to cyber security.
Ready to learn more?
Add the ChaosSearch Data Integration to Your Amazon Security Lake and discover how centralizing your logs in a cost-effective security data lake can complement your XDR solution.





