5 Ways to Use Log Analytics and Telemetry Data for Fraud Prevention
As fraud continues to grow in prevalence, SecOps teams are increasingly investing in fraud prevention capabilities to protect themselves and their customers.
One approach that’s proved reliable is the use of log analytics and telemetry data for fraud prevention. By collecting and analyzing data from various sources, including server logs, network traffic, and user behavior, enterprise SecOps teams can identify patterns and anomalies in real time that may indicate fraudulent activity.
The ability to detect fraudulent activity in real time often means that enterprise SecOps teams can block and investigate suspected fraudulent transactions before any significant damage is done.
In this article, we explore how enterprise SecOps teams are using log analytics and telemetry data for anomaly detection and fraud prevention, along with five fraud prevention use cases where log data can play a major role.

What is Fraud Prevention?
Fraud is a deliberate act of deception for personal gain. Fraudulent activities can take many forms, including financial fraud, identity theft or impersonation, credential theft, insurance fraud, cyber attacks, and many more.
Fraud prevention refers to the set of measures and strategies put in place to identify, prevent, and mitigate fraudulent activities. Fraud prevention aims to minimize the risk of these activities occurring, block fraudulent transactions whenever possible, and reduce the impact of any fraud that does occur.
High-scale, digital-native organizations need advanced technologies and infrastructure to effectively automate the detection of fraud at scale. With high volumes of data flowing through their systems and millions of transactions being processed daily, these organizations require sophisticated tools to identify and prevent fraudulent activities in real-time.
How To Enable Fraud Prevention with Log Analytics and Telemetry Data
1. Collecting and Aggregating Logs and Telemetry Data
Telemetry is the automated collection and transmission of data from remote devices or systems to a central location for analysis and monitoring. There are three types of telemetry data in computing: metrics, traces, and logs.
Metrics include measurements like CPU usage, memory utilization, network traffic, response times, and other details that indicate the health of applications or network infrastructure.
Traces are sequences of events or actions recorded as a series of data points. In modern software development, traces are often used in distributed systems where multiple services are involved in processing a single request or transaction. Traces can be used to understand the end-to-end flow of requests, identify the source of errors or issues, and optimize system performance.
Logs are machine-generated records containing detailed data about events or transactions that take place within an application, service, or network device. Logs provide a detailed record of system and application behavior, which can be used for troubleshooting, security, compliance, and performance monitoring.
The first step to using log analytics and telemetry data for fraud prevention is to aggregate metrics, traces, and logs from the organization’s network into a centralized database where it can be analyzed and correlated together.
Read: Understanding the Three Pillars of Observability: Logs, Metrics and Traces
2. Building a Fraud Detection Algorithm
Enterprise SecOps teams can leverage telemetry data aggregated from various sources (e.g. servers, network devices, applications, etc.) together with machine learning technology to develop a fraud detection algorithm.
Fraud detection algorithms process telemetry data to learn what constitutes normal behavior or a normal transaction, enabling them to identify anomalous behaviors and patterns that could indicate fraudulent activity.
Fraud detection algorithms can be integrated into the organization’s cyber security architecture and used to analyze telemetry data in real time for indicators of fraud. Ongoing monitoring and refinement of the algorithm are necessary to ensure its continued effectiveness as new types of fraud emerge and the system evolves.
3. Stream Processing Telemetry Data to Detect Fraudulent Activity
Enterprise SecOps teams can detect fraudulent activity using traditional batch processing methods, which require data to be collected over a period of time before analysis can be performed.
But to effectively prevent fraud, enterprise SecOps teams need stream processing: the ability to continuously analyze telemetry data using fraud detection algorithms in real time. Common stream analytics platforms include Apache Kafka Stream, Apache Flink, Google Cloud Dataflow, and Amazon Kinesis.
With stream processing, data can be analyzed as it is generated, enabling faster detection and response times to fraudulent activity. This is crucial in fraud detection, where even a small delay in detecting and responding to fraudulent activity can result in significant financial losses.
4. Alerting on Fraud and Blocking Fraudulent Transactions
With stream processing capabilities built into the organization’s security architecture, enterprise SecOps teams can detect anomalous or suspicious activity in real time, alert on suspected incidents of fraud, and automate the incident response process to block fraudulent transactions before they result in financial losses.
5. Persisting Telemetry Data for Long-Term Log Analytics Use Cases
Telemetry data that has been analyzed for fraud prevention can then be persisted into a long-term data store like Amazon S3 cloud object storage.
Historical telemetry data can be used to identify seasonal trends in usage patterns, discover the root cause of long-term performance issues, satisfy compliance and auditing requirements, and provide a record for forensic analysis in the event of a security breach or other system issue.
5 Fraud Prevention Use Cases for Log Analytics and Telemetry Data
1. Detecting Attacks on Cloud Infrastructure
Log analytics and telemetry data from cloud services can be used to detect fraudulent cyber attacks against an organization’s cloud infrastructure. By analyzing user behavior and event logs from cloud services in real-time, enterprise SecOps teams can identify login attempts from unfamiliar devices or IP addresses, multiple failed login attempts, suspicious data access patterns, or suspicious administrative activity that could indicate an account takeover attempt.
2. Detecting Fraudulent Mobile Phone Calls in Telecommunications
Telemetry data can be used to detect fraudulent mobile phone calls by analyzing call data records for patterns and anomalies. For example, high volumes of calls to premium-rate numbers or sudden spikes in international calls from a specific account can indicate fraudulent activity. By analyzing call data records in real-time, SecOps teams can detect and prevent fraud before significant financial losses occur.
3. Identifying Fraudulent Cash and Credit Transactions in Banking
Log analytics and telemetry data can be used to identify fraudulent cash and credit transactions in banking by monitoring transaction data for anomalies and suspicious patterns. For example, transactions that exceed a customer's typical spending patterns or transactions that occur in unusual locations can indicate fraudulent activity.
Fintech companies that process transactions online depend on some of the most complex fraud detection algorithms, factoring in everything from the user’s session data (browser, location, IP address, etc.) to their account information, transaction history, and numerous other factors to detect and prevent fraud.
4. Identifying Fraudulent Purchases in Retail or e-Commerce
Telemetry data can be used to identify fraudulent purchases in retail or e-commerce by analyzing transaction data for anomalies and suspicious patterns. SecOps teams can capture log and telemetry data from eCommerce transactional systems to alert on suspicious behaviors that could indicate fraud, including things like:
- Unusually large and expensive orders,
- Multiple orders being placed in a short period of time after changing a shipping address,
- Shipping and billing addresses not matching,
- Unusual payment methods for a specific customer,
- Suspicious requests for expedited shipping,
- Multiple failed attempts to process a payment,
- Using multiple credit cards to pay for a single order, and
- Orders placed from high-risk countries.
5. Detecting Healthcare Insurance Fraud
Log analytics and telemetry data can be used to detect healthcare insurance fraud by monitoring claims data for anomalies and suspicious patterns. Health insurance companies can train fraud detection algorithms to hone in on fraud indicators like excess and duplicate billing, overutilization of services or treatments, or kickback schemes orchestrated between patients and providers.
Read: Why SecOps Teams Need Security Log Analytics
Augment Your Fraud Prevention Capabilities with ChaosSearch
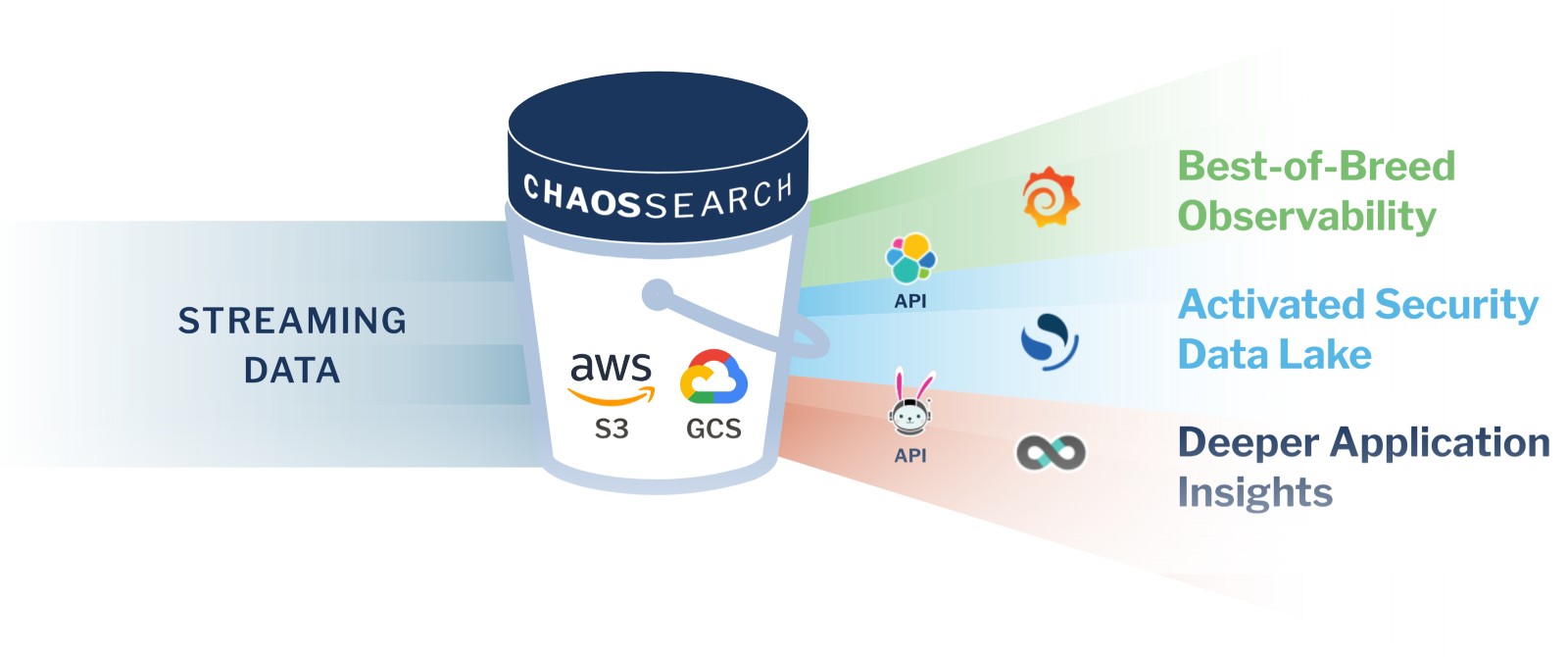
ChaosSearch is the foundation of a modern and future-proof cybersecurity architecture for your enterprise. Connecting directly to your existing Amazon S3 or GCS, ChaosSearch transforms your cloud object storage into a security data lake by indexing your historical logs and telemetry data for full searchability and SQL analytics with up to 95% data compression.
After stream processing telemetry data for real-time fraud prevention, enterprise SecOps teams can persist telemetry data in cloud object storage. ChaosSearch continually indexes log data as it arrives in cloud storage, enabling both long-term data storage for compliance purposes and near-real-time access for security operations and observability applications.
The unique technology and solution architecture of ChaosSearch delivers massively scalable and cost-effective security log analytics with no data movement and no limits on data retention, enabling use cases like advanced persistent threat hunting, DDoS attack identification, and root cause analysis of security incidents.